🔒 How to Secure Your API with Cloudflare API Shield and JWT Secrets
Securing APIs has never been more critical. As microservices proliferate and public APIs become more exposed, developers must ensure that only authorized clients can access protected resources. JSON Web Tokens (JWT) offer a scalable way to handle authentication, and Cloudflare’s API Shield makes it incredibly efficient to validate JWTs at the edge — before any request hits your infrastructure.
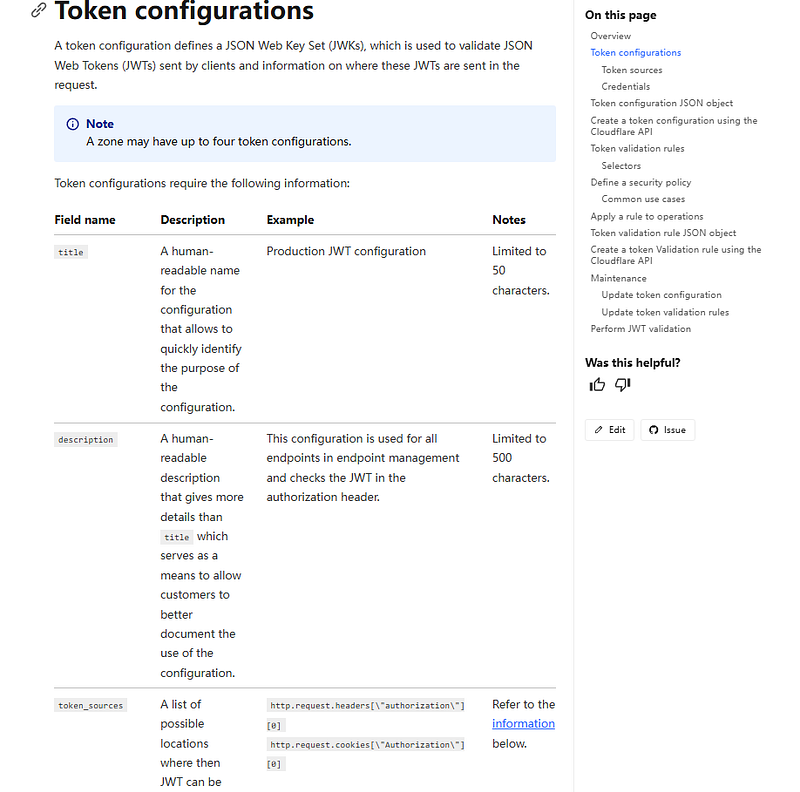
In this guide, you’ll learn how to combine Cloudflare API Shield’s JWT validation with secret management strategies using JWTSecrets.com. This combination provides maximum security and minimal latency for modern API deployments.
🔧 Why JWT + Cloudflare API Shield?
Traditional JWT validation usually happens within your backend logic. But Cloudflare’s API Shield lets you offload this responsibility to its edge network, filtering invalid requests before they reach your origin server. This not only reduces server load but also adds a critical layer of protection against unauthorized access and abuse.
Benefits:
- ✅ Reduced origin load
- ✅ Near-zero latency authentication
- ✅ Built-in secret rotation support
- ✅ Enhanced protection from abuse and token brute-forcing
🔐 What is JWTSecrets.com?
JWTSecrets.com is a developer-focused tool for generating and managing high-entropy secrets used for signing JWTs. Unlike common secret generators, JWTSecrets provides randomness tailored for cryptographic signing algorithms like HS256, ensuring that your tokens are tamper-proof.
Key Features:
- Strong, cryptographically secure JWT secrets
- Read-only history log to prevent accidental reuse
- Optional secret rotation reminders
🛠 Step-by-Step: JWT Validation with Cloudflare and JWTSecrets
Let’s walk through securing an API endpoint using a shared secret and HS256 JWT validation at the edge.
Step 1: Generate a Strong JWT Secret
- Go to jwtsecrets.com
- Select
HS256as your signing algorithm - Click Generate Secret
- Copy the secret value and securely store it (e.g., in Cloudflare dashboard and your auth server)
Tip: Use secrets with 256+ bits of entropy. Avoid simple, guessable strings.
Step 2: Issue JWTs on Your Auth Server
Here’s an example using Node.js:
const jwt = require('jsonwebtoken');
const payload = {
sub: "user_123",
role: "admin"
};
const secret = process.env.JWT_SECRET; // Your JWTSecrets.com key
const token = jwt.sign(payload, secret, {
algorithm: 'HS256',
expiresIn: '1h'
});Ensure your secret is stored securely in environment variables or a secrets vault.
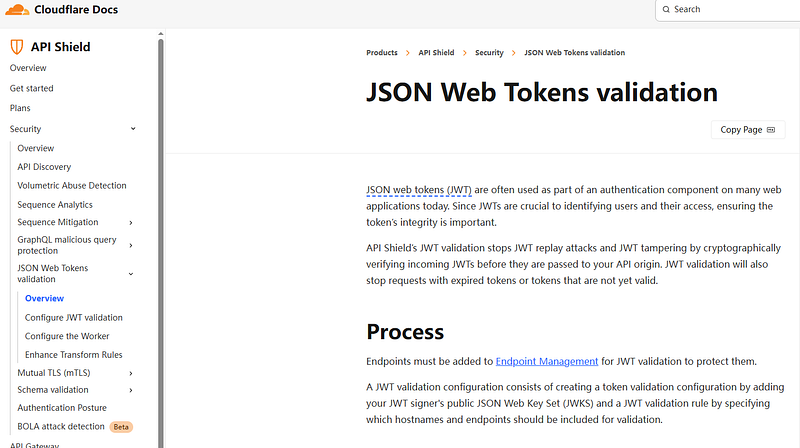
Step 3: Configure Cloudflare API Shield for JWT Validation
- Go to your Cloudflare Dashboard
- Select your site
- Navigate to Security → API Shield → JWT
- Click Create Rule
Fill in the following:
- Name:
JWT Protection Rule - Validation Algorithm:
HS256 - JWT Secret: Paste the secret from JWTSecrets
- Issuer (optional): Your issuer string if you use
issin payload - Audience (optional): If you specify
audin the JWT
⚠️ Cloudflare will validate the token at the edge. If it fails, it blocks the request.
Step 4: Apply the JWT Rule to Your API Paths
Still in the JWT validation rule:
- Match Request Path: Use something like
/api/* - Optionally, restrict by method (e.g., POST, GET)
- Save and enable the rule
From now on, any requests to /api/* must include a valid JWT like this:
httpGET /api/data HTTP/1.1
Authorization: Bearer <your-jwt-token>🔁 Bonus: Secret Rotation Strategy
Rotate your JWT secret periodically for enhanced security. Here’s a good workflow:
- Use JWTSecrets.com to generate a new secret
- Store the new secret in Cloudflare and your backend
- Start issuing tokens with the new secret
- Accept both old and new secrets temporarily during the transition
- After 1–2 hours, deprecate the old one
Cloudflare supports multiple secrets during rollout, which simplifies secret rotation.
📊 Real-World Use Case: Rate-Limited API with Token-Based Access
By using API Shield JWT validation:
- You can gate higher-tier access with specific
scopeorroleclaims. - Rate limiting can be customized per user by decoding tokens in your backend after they pass edge validation.
- Any requests without valid JWTs are blocked instantly, saving bandwidth and compute.
🧠 Final Thoughts
Integrating JWT validation into Cloudflare’s edge infrastructure is a no-brainer for performance and security. Combined with a tool like JWTSecrets.com for generating strong keys and maintaining good cryptographic hygiene, you’re building an API that’s secure by design.
If you’re serious about protecting your APIs and improving performance at scale, don’t skip this setup.
🙌 Enjoyed this tutorial?
Follow me on Medium at girff for more deep dives on edge security, API development, and backend best practices.
👉 Drop a like, leave a comment, and hit subscribe.
Let’s build safer, smarter APIs — together.



Member discussion